Blog
Data Breach
Section titled “Data Breach”🔐 Trends, Costs & Mitigation Strategies
It’s no longer a question of if, but when data breaches will occur. And their financial consequences are escalating rapidly.
📊 Key Statistics
| 68% of breaches involve human error (phishing, stolen credentials) |
| Software vulnerability attacks up 180% |
| AI-driven phishing campaigns surged 4,151% |
💸 Average Breach Cost by Sector
| Sector | Average Cost |
|---|---|
| Healthcare | $9.77M |
| Finance | $6.08M |
| Energy | $5.94M |
| Manufacturing | $5.56M |
| Government | $2.55M |
⏱️ Containment Time
| Average time to contain a breach: 258 days |
| If contained within 200 days, organizations save $1.39M |
🛡️ Top Mitigation Strategies
| Automation & AI → 31% cost reduction |
| Zero Trust Architecture → essential for finance & public sector |
| Network segmentation + MFA → critical for healthcare & retail |
| Continuous employee training → your first line of defense |
📅 Published on: August 2025
📣 Hashtags: #Cybersecurity #DataBreach2025 #RiskManagement #AI #ZeroTrust #Infosec

Age Verification Online
Section titled “Age Verification Online”🔐 Protecting Minors or Risking Digital Freedoms?
More and more countries are introducing laws to verify users’ age online, aiming to shield minors from harmful content. But are we truly building a safer internet, or paving the way for surveillance and discrimination?
🌍 Country Approaches to Age Verification
| Country | Measure |
|---|---|
| France | Access to adult sites blocked without age verification |
| Spain | Upcoming law mandates parental controls for social media |
| Italy | AGCOM introduced anonymous verification system |
| Greece | Launched KidsWallet app |
| Denmark | Proposed ban on social media under 15 |
| UK | Online Safety Act requires ID checks via documents, selfies, or digital IDs |
| Australia | Law bans social media under 16, fines up to $49.5M |
⚠️ Key Concerns
| Privacy: who controls the data, for how long, under what safeguards? |
| Algorithmic discrimination risks (documents, devices, bias) |
| Digital exclusion of vulnerable youth |
| Future repurposing of sensitive data (profiling, ads, services) |
🎯 Protecting minors is essential, but we must do so without compromising privacy, inclusion, and freedom of expression.
📅 Published on: July 2025
📣 Hashtags: #DigitalSafety #Privacy #OnlineAgeVerification #MinorsOnline #OnlineSafetyAct
Privacy-Focused Search Engines
Section titled “Privacy-Focused Search Engines”🛡️ In an era of increasing digital surveillance, choosing a search engine that respects your privacy is a strategic move.
✅ Alternatives to Google and Bing
| Engine | Description |
|---|---|
| DuckDuckGo | Does not track or store personal information; blocks website tracking |
| Brave Search | Own index; no tracking or profiling; unbiased results |
| Mojeek | Independent crawler and index; delivers unbiased search results |
| Qwant | European engine with strict GDPR compliance; privacy-first |
| Startpage | Proxy for Google results; anonymizes queries and IP addresses |
| Swisscows | Based in Switzerland; family-friendly and privacy-focused |
| Kagi | Paid service; anonymous searches; own index and anonymized APIs |
🔐 Key Features to Look For
| No IP address logging |
| No search history tracking |
| No personalized ads |
📅 Published on: June 2025
📣 Hashtags: #Privacy #SearchEngine #DataPrivacy #OnlineSecurity #PrivacyMatters #GDPR
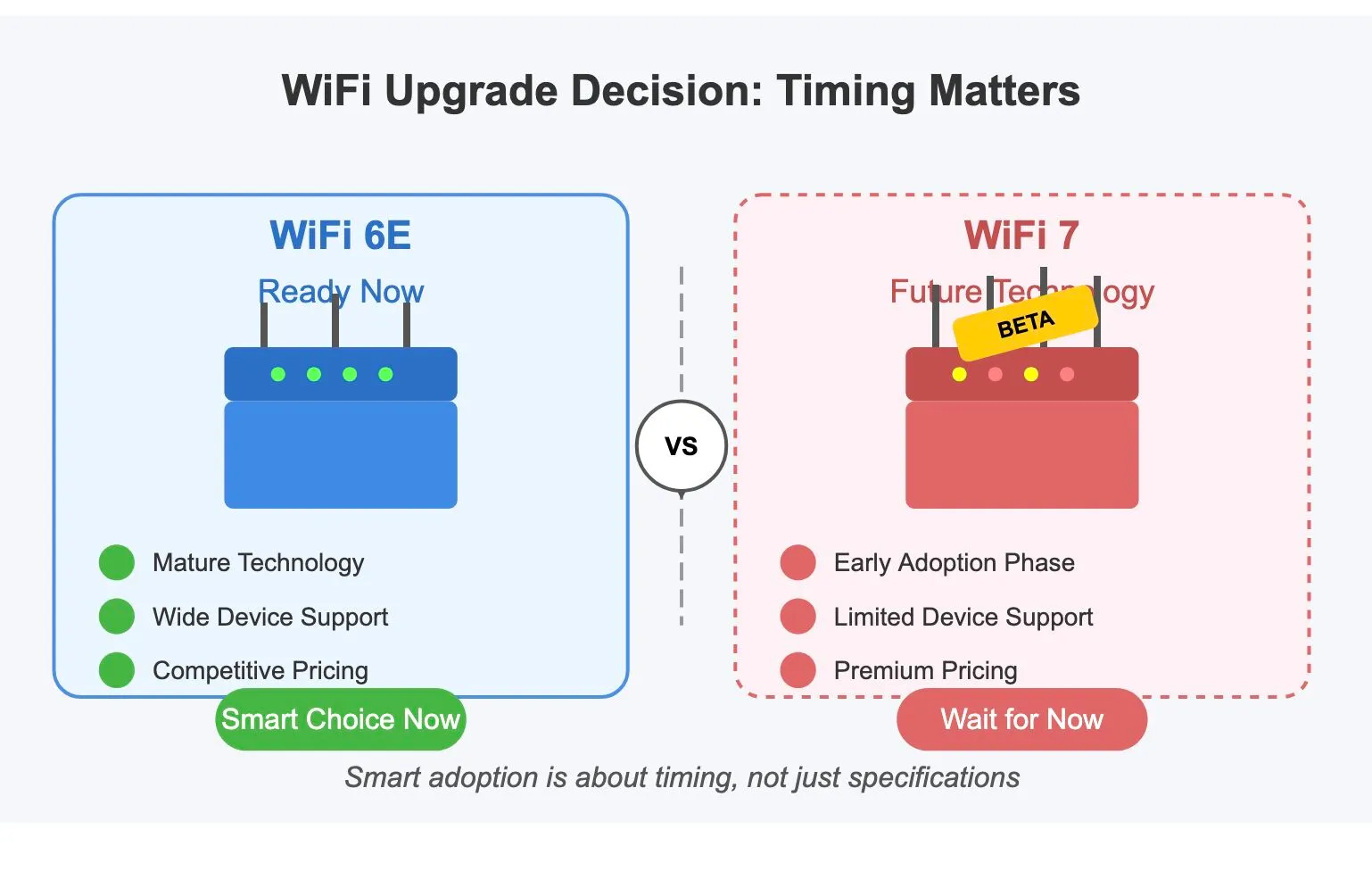
WiFi 7 vs WiFi 6E
Section titled “WiFi 7 vs WiFi 6E”📡 Why Jumping to WiFi 7 Might Not Be the Smart Move Just Yet
📶 While the tech world buzzes about WiFi 7’s capabilities, patience may be the wiser approach.
✅ Strategic Perspective
| Topic | Insight |
|---|---|
| WiFi 6E maturity | Tri-band WiFi 6E offers stable drivers, broad device support, proven reliability |
| Ecosystem readiness | Competitive pricing and mature deployments make WiFi 6E a safe investment |
| WiFi 7 limitations | Early adoption; standard not finalized; firmware and device support immature |
| Performance reality | Gains are mostly theoretical for typical business/home use cases |
| Adoption strategy | Prioritize reliability and cost-efficiency over hype |
| Future outlook | WiFi 7 is transitional — WiFi 8 may be the real leap (~2028) |
📅 Published on: May 2025
📣 Hashtags: #Networking #WiFi #TechnologyStrategy #DigitalInfrastructure #TechTrends
AI Image Generation: Beauty and Risk
Section titled “AI Image Generation: Beauty and Risk”🎨 The generation of images through AI — like the Studio Ghibli style trend — is fascinating.
🚨 Be mindful of the risks that come with this creative power.
⚠️ Risks
| Risk | Description |
|---|---|
| Non-transparent storage | Uploaded images may be stored and reused for unknown purposes |
| Deepfake expansion | Generated or uploaded images could be manipulated to create fake content |
| Sensitive data exposure | Hidden metadata (location, date, device) may reveal personal information |
📅 Published on: May 2025
📣 Hashtags: #AI #ArtificialIntelligence #Privacy #Deepfake #CyberSecurity #ChatGPT
Cybersec Investment in Europe
Section titled “Cybersec Investment in Europe”🚨 Global security trends are evolving rapidly
🔐 Cybersecurity is foundational to resilience and strategic growth.
🔟 Executive Points
| # | Topic | Insight |
|---|---|---|
| 1 | Escalating cyber threats | Risks are growing; investments must keep pace |
| 2 | Transatlantic collaboration | USA partnerships pivotal for defense |
| 3 | Strategic budgeting | Prioritize cybersecurity in financial planning |
| 4 | Workforce empowerment | Trained employees are first line of defense |
| 5 | Tailored technology | Choose tools aligned with needs |
| 6 | System updates | Regular patches and updates are non-negotiable |
| 7 | Regulatory compliance | Data protection laws stricter than ever |
| 8 | Shared responsibility | Cybersecurity is an organization-wide effort |
| 9 | Incident response | A solid plan minimizes impact and accelerates recovery |
| 10 | Future agility | Stay adaptable to emerging threats |
📅 Published on: April 2025
📣 Hashtags: #Cybersecurity #Cybersec #DataProtection #BusinessLeadership
